What is a DNS takeover?
DNS takeover vulnerabilities occur when a subdomain (subdomain.example.com) or domain has its authoritative nameserver set to a provider (e.g. AWS Route 53, Akamai, Microsoft Azure, etc.) but the hosted zone has been removed or deleted. Consequently, when making a request for DNS records the server responds with aSERVFAIL error. This allows an attacker to create the missing hosted zone on the service that was being used and thus control all DNS records for that (sub)domain. For example, if subdomain.example.com was pointing to a GitHub page and the user decided to delete their GitHub page, an attacker can now create a GitHub page, add a CNAME file containing subdomain.example.com, and claim subdomain.example.com.You can read more at: https://0xpatrik.com/subdomain-takeover-ns/
Source: indianajson/can-i-take-over-dns
Register
Register a new domaintakeover.us.kg and point NS to p04 (I randomly pick this).
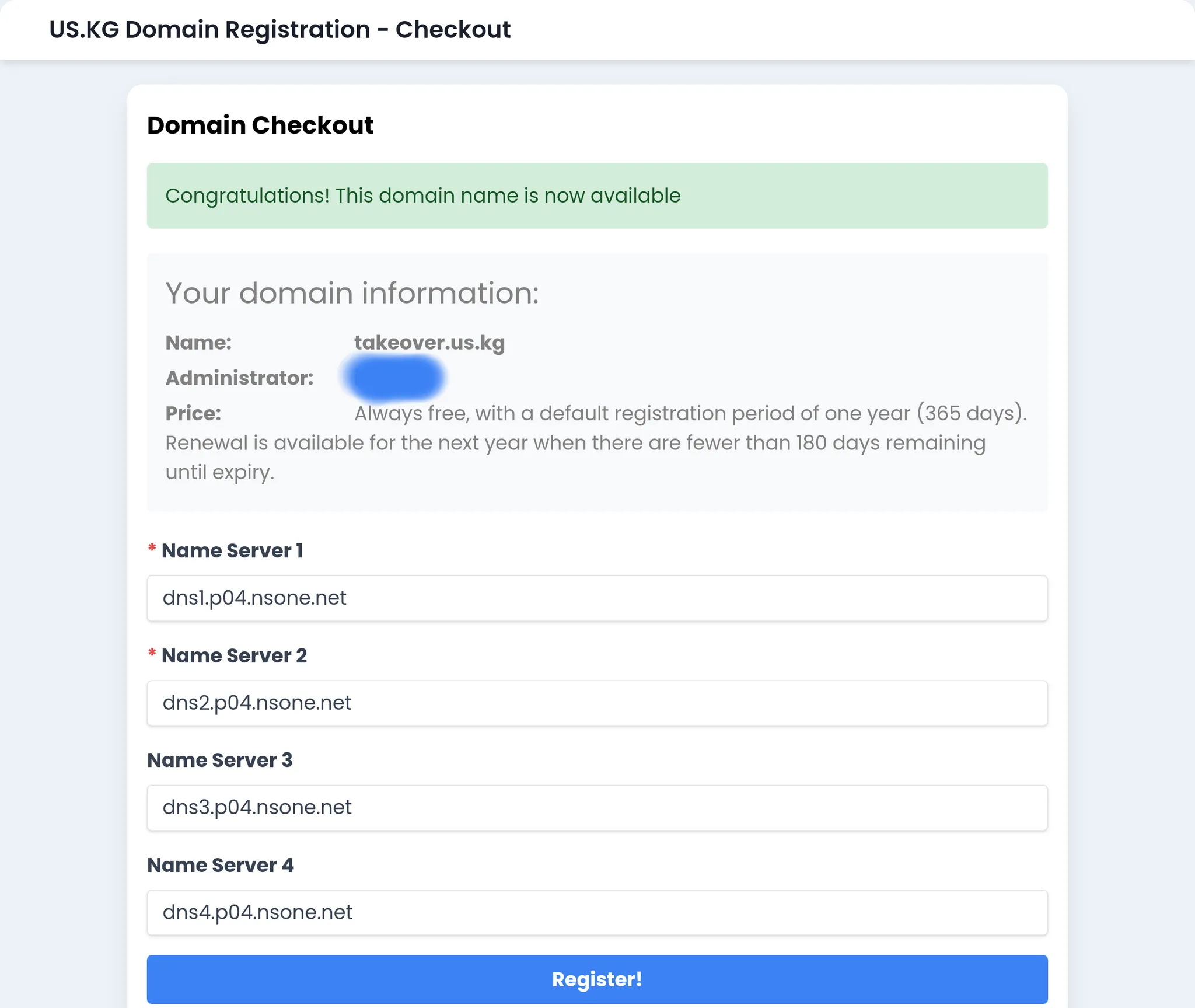
Add to NS1
Try to add new domain in NS1 panel.Case 1
Using non-administrator account.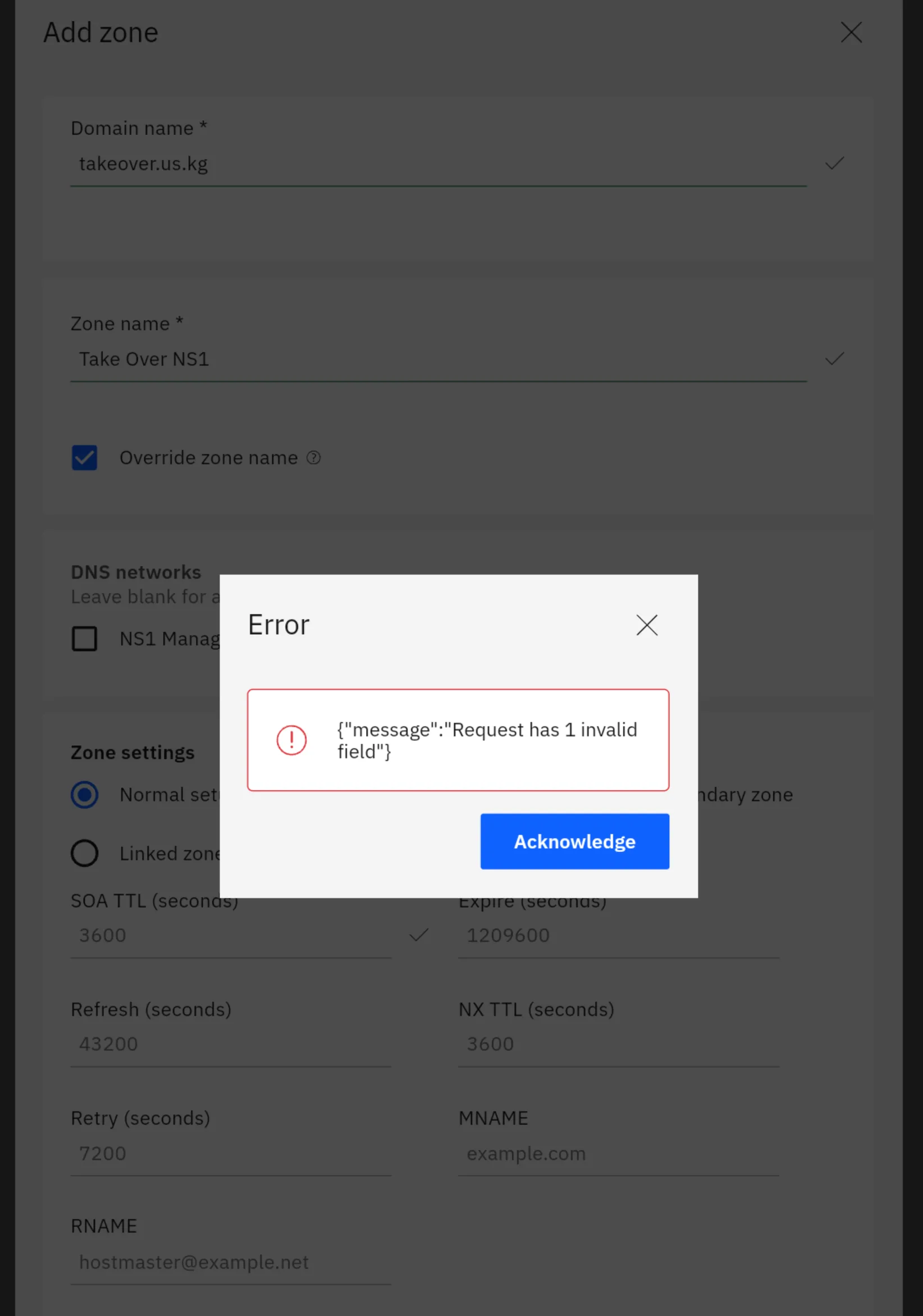 I don't know why this could happen. Non-administrator account have permission to manage all zones, and administrator account to manage all recourses.
I don't know why this could happen. Non-administrator account have permission to manage all zones, and administrator account to manage all recourses.Case 2
Using administrator account. Successfully add zone and got
Successfully add zone and got p07.Testing
Perform some tests.Dig NS
Try dig NS fortakeover.us.kg
dig NS +additional +trace takeover.us.kg. @208.67.222.222
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.15.tuxcare.els1 <<>> NS +additional +trace takeover.us.kg. @208.67.222.222
;; global options: +cmd
. 518400 IN NS a.root-servers.net.
. 518400 IN NS b.root-servers.net.
. 518400 IN NS c.root-servers.net.
. 518400 IN NS d.root-servers.net.
. 518400 IN NS e.root-servers.net.
. 518400 IN NS f.root-servers.net.
. 518400 IN NS g.root-servers.net.
. 518400 IN NS h.root-servers.net.
. 518400 IN NS i.root-servers.net.
. 518400 IN NS j.root-servers.net.
. 518400 IN NS k.root-servers.net.
. 518400 IN NS l.root-servers.net.
. 518400 IN NS m.root-servers.net.
. 518400 IN RRSIG NS 8 0 518400 20240726170000 20240713160000 20038 . M7vb1P9VxDe1RkPtHuYuWP9MSS7ovHwlY+t3P4b6ohdMjIwqh7VfCODX XRjN5N/5KDxz87+H8MtBLeRd4UgMfL86F9wQD0MdY7Lc3lHWe4qEGPU6 Uon/RMq9b6cJjMcc+aXd9hBkuLajBCwPtNqsXWRZ1Fp6UKIiq0avPR9h 6QMLIainz7QvFYPnfSxD0eK0P6eLaoAH/TJtD5ZjSFhzhVQKHCb0HAGu HuQrJCdV/61ckWP2LCDPJLrJZBveKRcUGvB1dZc+Nz0GXJ4bvdsVCik0 yPcwUh77G7uJLFehGrheQSHGFOeFtOyxw4ehToKpWLmWBdXdqlY6ChqZ 8b15Kg==
;; Received 525 bytes from 208.67.222.222#53(208.67.222.222) in 1 ms
kg. 172800 IN NS kg.cctld.authdns.ripe.net.
kg. 172800 IN NS ns.kg.
kg. 172800 IN NS ns2.kg.
kg. 86400 IN DS 45982 8 2 D642AF8C9BB761E035CE77A48750BBAA64B41CFA0799D8D94498CFA3 35FA1380
kg. 86400 IN RRSIG DS 8 1 86400 20240726170000 20240713160000 20038 . H+dj/G17dkkSI6k6kAiJDAkRE/wgnyGb/NSZi2Udr5pmu0y9wX1y/ZNT yLnkqDJJDDGDZfYcJeEOllUNX2rLWv/NudT35J/EOyiIComyxw0OSiAt X2a/isTHhgjldTbAS5qeY5+22bYqH999/fYZldwuPKSSZJuERcCHWm2K uPrhSofpTtmTLRHsLGPFJc85VFBeXwlhTOoAxXAZwWz/yCfXnuPo0iM5 d1HL8AnGbCJaPQVGrYas/kcWhNrLz+yQ8n5HkuWK1UF8UE+Om5d/+EDj 4HI3yrmS8PGrJ7IfDKN7iYXEYABVnZHGIZs32f3huJK6ixUvSeZ3F71r ozkplQ==
;; Received 584 bytes from 193.0.14.129#53(k.root-servers.net) in 14 ms
US.KG. 1800 IN NS NS2.DIGITALPLAT.ORG.
US.KG. 1800 IN NS NS4.DIGITALPLAT.ORG.
US.KG. 1800 IN NS NS1.DIGITALPLAT.ORG.
US.KG. 1800 IN NS NS3.DIGITALPLAT.ORG.
US.KG. 1800 IN NSEC USA.kg. NS RRSIG NSEC
US.KG. 1800 IN RRSIG NSEC 8 2 1800 20241231235953 20240713220013 3529 kg. ZVca/V2/RwNrnGwrpz6cTUiYmkTc066N8BOHX2dQM4YzeTsr0i2h/H6Z j+mjMqBMvdz7ozrdcQqAgedTSQmOvuG+YG+vbrYuRIvj+czVPqfucXM8 pX1Ks6u51/AmYGptMDaBA3HsAUjjBkWp1u0NLJLch+WSih2aaKADnZY0 6+vB3qBr5F0eqDkhwyqZANMlPz3UoWqX8t6LdKzgdQbsQM14+Z3iS4O3 rdcD/i5ARTKAMaol5CSSnpZGSRtGnYdxLqSX7akfbSJI1sfI7uc8/3LS OUxpANJmUJcbgm6SvoVVQuyeu61eFeTi6AP0778gM1BxbWDfo9D1W++0 ksM36A==
;; Received 453 bytes from 195.38.160.38#53(ns2.kg) in 183 ms
takeover.us.kg. 3600 IN NS dns3.p04.nsone.net.
takeover.us.kg. 3600 IN NS dns4.p04.nsone.net.
takeover.us.kg. 3600 IN NS dns1.p04.nsone.net.
takeover.us.kg. 3600 IN NS dns2.p04.nsone.net.
;; Received 132 bytes from 150.230.46.101#53(NS1.DIGITALPLAT.ORG) in 51 ms
takeover.us.kg. 3600 IN NS dns1.p07.nsone.net.
takeover.us.kg. 3600 IN NS dns2.p07.nsone.net.
takeover.us.kg. 3600 IN NS dns3.p07.nsone.net.
takeover.us.kg. 3600 IN NS dns4.p07.nsone.net.
;; Received 132 bytes from 198.51.44.4#53(dns1.p04.nsone.net) in 2 ms
Add TXT
Try to add TXT record and perform dig TXT
dig TXT +additional +trace takeover.us.kg. @208.67.222.222
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.15.tuxcare.els1 <<>> TXT +additional +trace takeover.us.kg. @208.67.222.222
#################################################
takeover.us.kg. 3600 IN NS dns3.p04.nsone.net.
takeover.us.kg. 3600 IN NS dns4.p04.nsone.net.
takeover.us.kg. 3600 IN NS dns1.p04.nsone.net.
takeover.us.kg. 3600 IN NS dns2.p04.nsone.net.
;; Received 132 bytes from 150.230.46.101#53(NS1.DIGITALPLAT.ORG) in 51 ms
takeover.us.kg. 60 IN TXT "NS1 Take Over DNS"
;; Received 73 bytes from 198.51.45.4#53(dns2.p04.nsone.net) in 3 ms